The most secure Windows ever. Windows 10 provides comprehensive, built-in protection—at no extra cost. 1 Learn how Windows Hello facial recognition and biometric logins, coupled with comprehensive antivirus protection, keep you more secure than ever. The modification of security settings in Active Directory and the registry and other databases; The modification of permissions on objects in AD, the file system, the Windows registry; Note that the security settings can be defined on the local, a remote computer, an interoperability mismatch between the local and a remote computer.
-->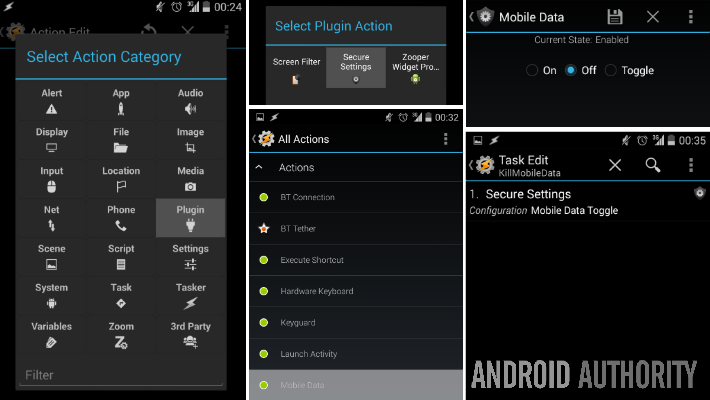
Secure Settings is a Locale/Tasker/Llama compatible plugin for Android 2.2+ Please see the changelog for updates Secure Settings Pro Trial licenses are available! Click the menu button inside of. Manage Security Settings Security icon: Zoom’s security features, which had previously been accessed throughout the meeting menus, are now grouped together and found by clicking the Security icon in the meeting menu bar on the host's interface. You can also lock the Screen Share by default for all your meetings in your web settings.
Settings.secure.location_providers_allowed
Applies to
- Windows 10
Provides an introduction to the Security Options settings for local security policies and links to more information.
The Security Options contain the following groupings of security policy settings that allow you to configure the behavior of the local computer. Some of these policies can be included in a Group Policy Object and distributed over your organization.
Cooking dash cheat your way comp. When you edit policy settings locally on a device, you only affect the settings on only that device. If you configure the settings in a Group Policy Object (GPO), the settings apply to all devices that are subject to that GPO.
Secure Proxy Settings
For info about setting security policies, see Configure security policy settings.
In this section
Securecrt Proxy Settings
| Article | Description |
|---|---|
| Accounts: Administrator account status | Describes the best practices, location, values, and security considerations for the Accounts: Administrator account status security policy setting. |
| Accounts: Block Microsoft accounts | Describes the best practices, location, values, management, and security considerations for the Accounts: Block Microsoft accounts security policy setting. |
| Accounts: Guest account status | Describes the best practices, location, values, and security considerations for the Accounts: Guest account status security policy setting. |
| Accounts: Limit local account use of blank passwords to console logon only | Describes the best practices, location, values, and security considerations for the Accounts: Limit local account use of blank passwords to console logon only security policy setting. |
| Accounts: Rename administrator account | This security policy article for the IT professional describes the best practices, location, values, and security considerations for this policy setting. |
| Accounts: Rename guest account | Describes the best practices, location, values, and security considerations for the Accounts: Rename guest account security policy setting. |
| Audit: Audit the access of global system objects | Describes the best practices, location, values, and security considerations for the Audit: Audit the access of global system objects security policy setting. |
| Audit: Audit the use of Backup and Restore privilege | Describes the best practices, location, values, and security considerations for the Audit: Audit the use of Backup and Restore privilege security policy setting. |
| Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings | Describes the best practices, location, values, and security considerations for the Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings security policy setting. |
| Audit: Shut down system immediately if unable to log security audits | Describes the best practices, location, values, management practices, and security considerations for the Audit: Shut down system immediately if unable to log security audits security policy setting. |
| DCOM: Machine Access Restrictions in Security Descriptor Definition Language (SDDL) syntax | Describes the best practices, location, values, and security considerations for the DCOM: Machine Access Restrictions in Security Descriptor Definition Language (SDDL) syntax policy setting. |
| DCOM: Machine Launch Restrictions in Security Descriptor Definition Language (SDDL) syntax | Describes the best practices, location, values, and security considerations for the DCOM: Machine Launch Restrictions in Security Descriptor Definition Language (SDDL) syntax security policy setting. |
| Devices: Allow undock without having to log on | Describes the best practices, location, values, and security considerations for the Devices: Allow undock without having to log on security policy setting. |
| Devices: Allowed to format and eject removable media | Describes the best practices, location, values, and security considerations for the Devices: Allowed to format and eject removable media security policy setting. |
| Devices: Prevent users from installing printer drivers | Describes the best practices, location, values, and security considerations for the Devices: Prevent users from installing printer drivers security policy setting. |
| Devices: Restrict CD-ROM access to locally logged-on user only | Describes the best practices, location, values, and security considerations for the Devices: Restrict CD-ROM access to locally logged-on user only security policy setting. |
| Devices: Restrict floppy access to locally logged-on user only | Describes the best practices, location, values, and security considerations for the Devices: Restrict floppy access to locally logged-on user only security policy setting. |
| Domain controller: Allow server operators to schedule tasks | Describes the best practices, location, values, and security considerations for the Domain controller: Allow server operators to schedule tasks security policy setting. |
| Domain controller: LDAP server signing requirements | Describes the best practices, location, values, and security considerations for the Domain controller: LDAP server signing requirements security policy setting. |
| Domain controller: Refuse machine account password changes | Describes the best practices, location, values, and security considerations for the Domain controller: Refuse machine account password changes security policy setting. |
| Domain member: Digitally encrypt or sign secure channel data (always) | Describes the best practices, location, values, and security considerations for the Domain member: Digitally encrypt or sign secure channel data (always) security policy setting. |
| Domain member: Digitally encrypt secure channel data (when possible) | Describes the best practices, location, values, and security considerations for the Domain member: Digitally encrypt secure channel data (when possible) security policy setting. |
| Domain member: Digitally sign secure channel data (when possible) | Describes the best practices, location, values, and security considerations for the Domain member: Digitally sign secure channel data (when possible) security policy setting. |
| Domain member: Disable machine account password changes | Describes the best practices, location, values, and security considerations for the Domain member: Disable machine account password changes security policy setting. |
| Domain member: Maximum machine account password age | Describes the best practices, location, values, and security considerations for the Domain member: Maximum machine account password age security policy setting. |
| Domain member: Require strong (Windows 2000 or later) session key | Describes the best practices, location, values, and security considerations for the Domain member: Require strong (Windows 2000 or later) session key security policy setting. |
| Interactive logon: Display user information when the session is locked | Describes the best practices, location, values, and security considerations for the Interactive logon: Display user information when the session is locked security policy setting. |
| Interactive logon: Don't display last signed-in | Describes the best practices, location, values, and security considerations for the Interactive logon: Don't display last signed-in security policy setting. |
| Interactive logon: Don't display username at sign-in | Describes the best practices, location, values, and security considerations for the Interactive logon: Do not display username at sign-in security policy setting. |
| Interactive logon: Do not require CTRL+ALT+DEL | Describes the best practices, location, values, and security considerations for the Interactive logon: Do not require CTRL+ALT+DEL security policy setting. |
| Interactive logon: Machine account lockout threshold | Describes the best practices, location, values, management, and security considerations for the Interactive logon: Machine account lockout threshold security policy setting. |
| Interactive logon: Machine inactivity limit | Describes the best practices, location, values, management, and security considerations for the Interactive logon: Machine inactivity limit security policy setting. |
| Interactive logon: Message text for users attempting to log on | Describes the best practices, location, values, management, and security considerations for the Interactive logon: Message text for users attempting to log on security policy setting. |
| Interactive logon: Message title for users attempting to log on | Describes the best practices, location, values, policy management, and security considerations for the Interactive logon: Message title for users attempting to log on security policy setting. |
| Interactive logon: Number of previous logons to cache (in case domain controller is not available) | Describes the best practices, location, values, policy management, and security considerations for the Interactive logon: Number of previous logons to cache (in case domain controller is not available) security policy setting. |
| Interactive logon: Prompt user to change password before expiration | Describes the best practices, location, values, policy management, and security considerations for the Interactive logon: Prompt user to change password before expiration security policy setting. |
| Interactive logon: Require Domain Controller authentication to unlock workstation | Describes the best practices, location, values, policy management, and security considerations for the Interactive logon: Require Domain Controller authentication to unlock workstation security policy setting. |
| Interactive logon: Require smart card | Describes the best practices, location, values, policy management, and security considerations for the Interactive logon: Require smart card security policy setting. |
| Interactive logon: Smart card removal behavior | Describes the best practices, location, values, policy management, and security considerations for the Interactive logon: Smart card removal behavior security policy setting. |
| Microsoft network client: Digitally sign communications (always) | Describes the best practices, location, values, policy management, and security considerations for the Microsoft network client: Digitally sign communications (always) security policy setting for SMBv3 and SMBv2. |
| SMBv1 Microsoft network client: Digitally sign communications (always) | Describes the best practices, location, values, policy management, and security considerations for the Microsoft network client: Digitally sign communications (always) security policy setting for SMBv1 only. |
| SMBv1 Microsoft network client: Digitally sign communications (if server agrees) | Describes the best practices, location, values, and security considerations for the Microsoft network client: Digitally sign communications (if server agrees) security policy setting for SMBv1 only. |
| Microsoft network client: Send unencrypted password to third-party SMB servers | Describes the best practices, location, values, policy management, and security considerations for the Microsoft network client: Send unencrypted password to third-party SMB servers security policy setting. |
| Microsoft network server: Amount of idle time required before suspending session | Describes the best practices, location, values, and security considerations for the Microsoft network server: Amount of idle time required before suspending session security policy setting. |
| Microsoft network server: Attempt S4U2Self to obtain claim information | Describes the best practices, location, values, management, and security considerations for the Microsoft network server: Attempt S4U2Self to obtain claim information security policy setting. |
| Microsoft network server: Digitally sign communications (always) | Describes the best practices, location, values, policy management, and security considerations for the Microsoft network server: Digitally sign communications (always) security policy setting for SMBv3 and SMBv2. |
| SMBv1 Microsoft network server: Digitally sign communications (always) | Describes the best practices, location, values, policy management, and security considerations for the Microsoft network server: Digitally sign communications (always) security policy setting for SMBv1 only. |
| SMBv1 Microsoft network server: Digitally sign communications (if client agrees) | Describes the best practices, location, values, policy management, and security considerations for the Microsoft network server: Digitally sign communications (if client agrees) security policy setting for SMBv1 only. |
| Microsoft network server: Disconnect clients when logon hours expire | Describes the best practices, location, values, and security considerations for the Microsoft network server: Disconnect clients when logon hours expire security policy setting. |
| Microsoft network server: Server SPN target name validation level | Describes the best practices, location, and values, policy management, and security considerations for the Microsoft network server: Server SPN target name validation level security policy setting. |
| Network access: Allow anonymous SID/Name translation | Describes the best practices, location, values, policy management, and security considerations for the Network access: Allow anonymous SID/Name translation security policy setting. |
| Network access: Do not allow anonymous enumeration of SAM accounts | Describes the best practices, location, values, and security considerations for the Network access: Do not allow anonymous enumeration of SAM accounts security policy setting. |
| Network access: Do not allow anonymous enumeration of SAM accounts and shares | Describes the best practices, location, values, and security considerations for the Network access: Do not allow anonymous enumeration of SAM accounts and shares security policy setting. |
| Network access: Do not allow storage of passwords and credentials for network authentication | Describes the best practices, location, values, policy management, and security considerations for the Network access: Do not allow storage of passwords and credentials for network authentication security policy setting. |
| Network access: Let Everyone permissions apply to anonymous users | Describes the best practices, location, values, policy management, and security considerations for the Network access: Let Everyone permissions apply to anonymous users security policy setting. |
| Network access: Named Pipes that can be accessed anonymously | Describes the best practices, location, values, policy management, and security considerations for the Network access: Named Pipes that can be accessed anonymously security policy setting. |
| Network access: Remotely accessible registry paths | Describes the best practices, location, values, policy management, and security considerations for the Network access: Remotely accessible registry paths security policy setting. |
| Network access: Remotely accessible registry paths and subpaths | Describes the best practices, location, values, and security considerations for the Network access: Remotely accessible registry paths and subpaths security policy setting. |
| Network access: Restrict anonymous access to Named Pipes and Shares | Describes the best practices, location, values, policy management, and security considerations for the Network access: Restrict anonymous access to Named Pipes and Shares security policy setting. |
| Network access: Restrict clients allowed to make remote calls to SAM | Describes the best practices, location, values, policy management, and security considerations for the Network access: Restrict clients allowed to make remote calls to SAM security policy setting. |
| Network access: Shares that can be accessed anonymously | Describes the best practices, location, values, policy management, and security considerations for the Network access: Shares that can be accessed anonymously security policy setting. |
| Network access: Sharing and security model for local accounts | Describes the best practices, location, values, policy management, and security considerations for the Network access: Sharing and security model for local accounts security policy setting. |
| Network security: Allow Local System to use computer identity for NTLM | Describes the location, values, policy management, and security considerations for the Network security: Allow Local System to use computer identity for NTLM security policy setting. |
| Network security: Allow LocalSystem NULL session fallback | Describes the best practices, location, values, and security considerations for the Network security: Allow LocalSystem NULL session fallback security policy setting. |
| Network security: Allow PKU2U authentication requests to this computer to use online identities | Describes the best practices, location, and values for the Network Security: Allow PKU2U authentication requests to this computer to use online identities security policy setting. |
| Network security: Configure encryption types allowed for Kerberos Win7 only | Describes the best practices, location, values, and security considerations for the Network security: Configure encryption types allowed for Kerberos Win7 only security policy setting. |
| Network security: Do not store LAN Manager hash value on next password change | Describes the best practices, location, values, policy management, and security considerations for the Network security: Do not store LAN Manager hash value on next password change security policy setting. |
| Network security: Force logoff when logon hours expire | Describes the best practices, location, values, policy management, and security considerations for the Network security: Force logoff when logon hours expire security policy setting. |
| Network security: LAN Manager authentication level | Describes the best practices, location, values, policy management, and security considerations for the Network security: LAN Manager authentication level security policy setting. |
| Network security: LDAP client signing requirements | This security policy reference topic for the IT professional describes the best practices, location, values, policy management, and security considerations for this policy setting. This information applies to computers running at least the Windows Server 2008 operating system. |
| Network security: Minimum session security for NTLM SSP based (including secure RPC) clients | Describes the best practices, location, values, policy management, and security considerations for the Network security: Minimum session security for NTLM SSP based (including secure RPC) clients security policy setting. |
| Network security: Minimum session security for NTLM SSP based (including secure RPC) servers | Describes the best practices, location, values, policy management, and security considerations for the Network security: Minimum session security for NTLM SSP based (including secure RPC) servers security policy setting. |
| Network security: Restrict NTLM: Add remote server exceptions for NTLM authentication | Describes the best practices, location, values, management aspects, and security considerations for the Network security: Restrict NTLM: Add remote server exceptions for NTLM authentication security policy setting. |
| Network security: Restrict NTLM: Add server exceptions in this domain | Describes the best practices, location, values, management aspects, and security considerations for the Network security: Restrict NTLM: Add server exceptions in this domain security policy setting. |
| Network security: Restrict NTLM: Audit incoming NTLM traffic | Describes the best practices, location, values, management aspects, and security considerations for the Network Security: Restrict NTLM: Audit incoming NTLM traffic security policy setting. |
| Network security: Restrict NTLM: Audit NTLM authentication in this domain | Describes the best practices, location, values, management aspects, and security considerations for the Network Security: Restrict NTLM: Audit NTLM authentication in this domain security policy setting. |
| Network security: Restrict NTLM: Incoming NTLM traffic | Describes the best practices, location, values, management aspects, and security considerations for the Network Security: Restrict NTLM: Incoming NTLM traffic security policy setting. |
| Network security: Restrict NTLM: NTLM authentication in this domain | Describes the best practices, location, values, management aspects, and security considerations for the Network Security: Restrict NTLM: NTLM authentication in this domain security policy setting. |
| Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers | Describes the best practices, location, values, management aspects, and security considerations for the Network Security: Restrict NTLM: Outgoing NTLM traffic to remote servers security policy setting. |
| Recovery console: Allow automatic administrative logon | Describes the best practices, location, values, policy management, and security considerations for the Recovery console: Allow automatic administrative logon security policy setting. |
| Recovery console: Allow floppy copy and access to all drives and folders | Describes the best practices, location, values, policy management, and security considerations for the Recovery console: Allow floppy copy and access to all drives and folders security policy setting. |
| Shutdown: Allow system to be shut down without having to lg on | Describes the best practices, location, values, policy management, and security considerations for the Shutdown: Allow system to be shut down without having to log on security policy setting. |
| Shutdown: Clear virtual memory pagefile | Describes the best practices, location, values, policy management, and security considerations for the Shutdown: Clear virtual memory pagefile security policy setting. |
| System cryptography: Force strong key protection for user keys stored on the computer | Describes the best practices, location, values, policy management, and security considerations for the System cryptography: Force strong key protection for user keys stored on the computer security policy setting. |
| System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing | This security policy reference topic for the IT professional describes the best practices, location, values, policy management, and security considerations for this policy setting. |
| System objects: Require case insensitivity for non-Windows subsystems | Describes the best practices, location, values, policy management, and security considerations for the System objects: Require case insensitivity for non-Windows subsystems security policy setting. |
| System objects: Strengthen default permissions of internal system objects (e.g. Symbolic Links) | Describes the best practices, location, values, policy management, and security considerations for the System objects: Strengthen default permissions of internal system objects (for example, Symbolic Links) security policy setting. |
| System settings: Optional subsystems | Describes the best practices, location, values, policy management, and security considerations for the System settings: Optional subsystems security policy setting. |
| System settings: Use certificate rules on Windows executables for Software Restriction Policies | Describes the best practices, location, values, policy management, and security considerations for the System settings: Use certificate rules on Windows executables for Software Restriction Policies security policy setting. |
| User Account Control: Admin Approval Mode for the Built-in Administrator account | Describes the best practices, location, values, policy management, and security considerations for the User Account Control: Admin Approval Mode for the Built-in Administrator account security policy setting. |
| User Account Control: Allow UIAccess applications to prompt for elevation without using the secure desktop | Describes the best practices, location, values, and security considerations for the User Account Control: Allow UIAccess applications to prompt for elevation without using the secure desktop security policy setting. |
| User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode | Describes the best practices, location, values, policy management, and security considerations for the User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode security policy setting. |
| User Account Control: Behavior of the elevation prompt for standard users | Describes the best practices, location, values, policy management, and security considerations for the User Account Control: Behavior of the elevation prompt for standard users security policy setting. |
| User Account Control: Detect application installations and prompt for elevation | Describes the best practices, location, values, policy management, and security considerations for the User Account Control: Detect application installations and prompt for elevation security policy setting. |
| User Account Control: Only elevate executables that are signed and validated | Describes the best practices, location, values, policy management, and security considerations for the User Account Control: Only elevate executables that are signed and validated security policy setting. |
| User Account Control: Only elevate UIAccess applications that are installed in secure locations | Describes the best practices, location, values, policy management, and security considerations for the User Account Control: Only elevate UIAccess applications that are installed in secure locations security policy setting. |
| User Account Control: Run all administrators in Admin Approval Mode | Describes the best practices, location, values, policy management, and security considerations for the User Account Control: Run all administrators in Admin Approval Mode security policy setting. |
| User Account Control: Switch to the secure desktop when prompting for elevation | Describes the best practices, location, values, policy management, and security considerations for the User Account Control: Switch to the secure desktop when prompting for elevation security policy setting. |
| User Account Control: Virtualize file and registry write failures to per-user locations | Describes the best practices, location, values, policy management, and security considerations for the User Account Control: Virtualize file and registry write failures to per-user locations security policy setting. |
دانلود Secure Settings Pro
Related articles
